Today’s businesses rely heavily on their digital assets and information systems to operate efficiently. However, this reliance exposes them to a number of risks, ...
Blog - July 2023: Why ISO 19770-1 can be a strong ally in Risk Management (ISO 27001)
... including security breaches, unauthorized use of assets, and data loss. In this blog, we’ll explore the relationship between Risk Management, Security, and IT Asset Management (ITAM) as outlined in the ISO 19770-1 and ISO 27001 standards.
The Risk Management sphere
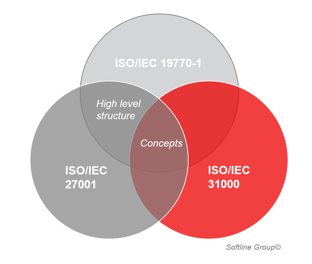
Risk management is a systematic process that organizations use to identify, assess, and mitigate potential threats that could negatively impact their operations. By taking proactive measures, businesses can minimize vulnerabilities and protect their valuable assets, including digital resources and sensitive data. Just like with ITAM and Security Management, there is no need to re-invent the wheel as best practices for risk assessments have been described in the ISO 31000. Even though the ISO 31000 does not share the same high level structure, the basic concepts are the same and there is a considerable overlap in processes and approach for risk management.
The IT Asset Management sphere
The ISO 19770-1 standard provides guidelines for IT Asset Management. It helps organizations achieve efficient management of their digital resources. By adopting ISO 19770-1 principles, businesses can ensure accurate inventory tracking, software license compliance, and effective planning for technology upgrades. Proper ITAM contributes to Risk Management because it enables businesses to understand their technological landscape better, prevent unauthorized usage, and reduce the risk of non-compliance with licensing agreements. The link to Security Management lies predominantly in their shared interest in the location, status and patch levels of assets.
The Security Management sphere
The connection between Security- and IT Asset Management lies in their collective effort to mitigate risks. Effective ITAM can strengthen security by enabling organizations to maintain an up-to-date inventory of software and hardware. By understanding their technology landscape, businesses can identify potential security or asset vulnerabilities and proactively address them.
On the other hand, robust security measures directly impact IT Asset Management. By safeguarding sensitive data and information systems, businesses can prevent unauthorized access to critical assets. In addition, security protocols can enhance compliance with licensing agreements and reduce the risk of potential legal issues stemming from improper asset management or unauthorized use of assets. Their joint efforts are of great importance to Risk Management, by providing tangible results and sound processes to fill in the framework ISO 31000 provides.
In conclusion:
In the modern business landscape, Risk Management is crucial for organizations seeking to safeguard their digital assets and sensitive data. The overlapping spheres of Security and IT Asset Management, as outlined in ISO 19770-1 and ISO 27001, provide businesses with a comprehensive approach to identify and address potential risks. By performing Risk Management procedures organizations can gather insights in the risk associated to Security and IT Asset Management, organizations can build resilience against various threats, protect their assets, and ensure the continuity of their operations.
Softline can help with consulting, services and even tooling that supports ISO conformity. Curious about how we can help? Give us a call!
Book a free meeting with our lead consultant for ISO: Ash Dharas
More on ISO certification and its benefits:
- Essential steps to prepare for ISO 19770-1 certification
- How ISO/IEC19770-1 certification can help during internal audits
- How ISO/IEC19770-1 certification can help achieve management buy-in
- What is the ITAM team doing exactly? Continuous improvement apparently
- Quality assurance through ISO 19770-1 certification
- ISO certification: Is my ITAM practice ready?
